使用http访问自己搭建的服务时,浏览器会出现不安全相关提示,体验感比较差,因此需要想办法生成https的证书
前情提要
- VPS Ubuntu24.04 LTS
- VPS 拥有公网IP
- 拥有自己的域名(使用mr-h.org举例)
- VPS已经安装好nginx,headscale,headscale web ui
- 生成证书的工具为cerbot(生成p2p.mr-h.org的证书)
- 以下均在VPS上进行
安装cerbot
- 安装certbot相关包
1
2
| sudo apt update
sudo apt install certbot python3-certbot-nginx
|
配置域名解析和域名解析代理策略
- 在cloudflare中添加二级域名,并指向自己服务器的ip
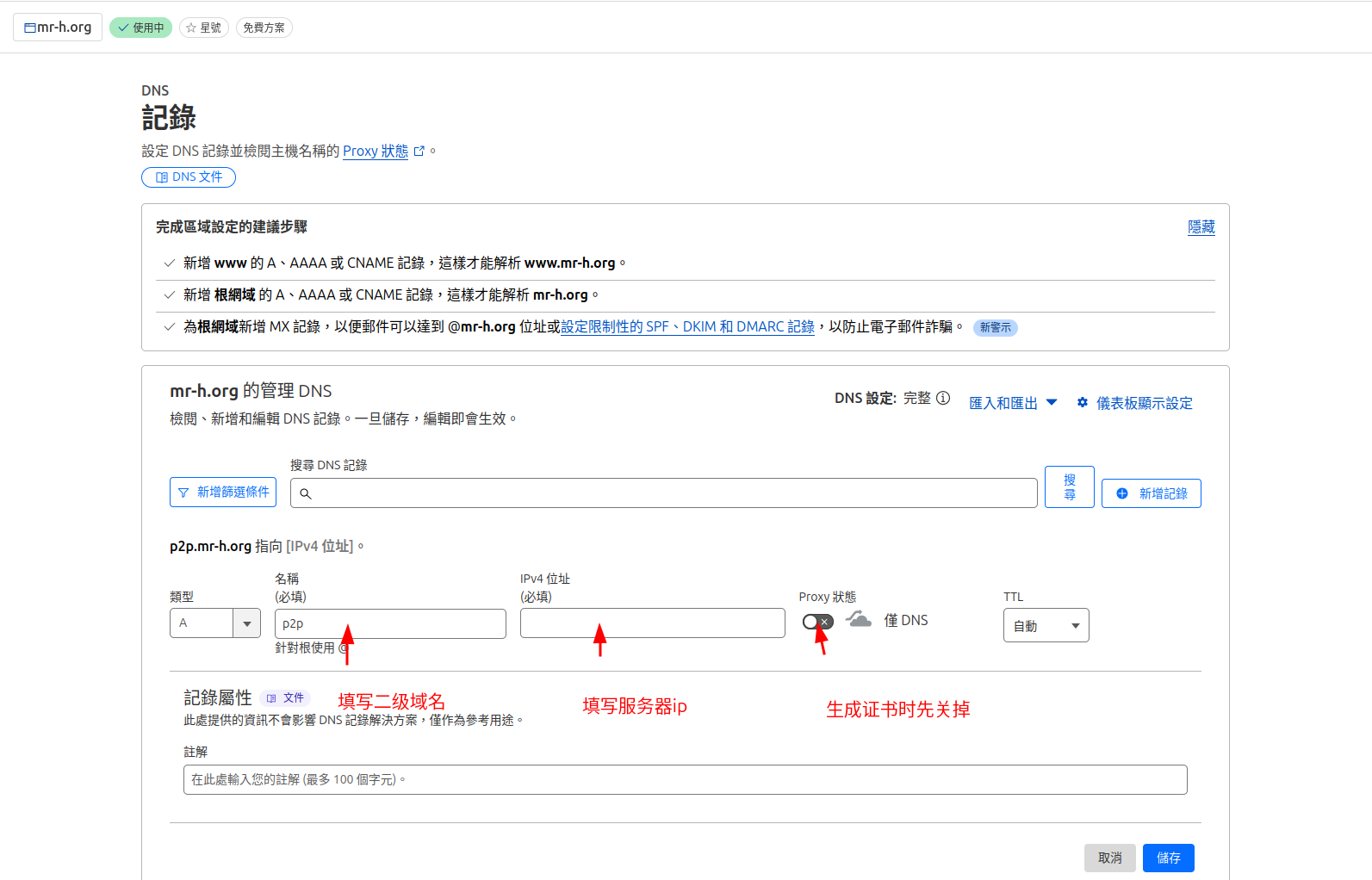
- 在cloudflare中修改代理策略为严格。(注意:如果选择灵活可能会导致申请证书后,使用https访问出现代理次数过多的错误)

nginx配置
- 在/etc/nginx/sites-available 创建headscale的进包含http服务的配置,配置内容如下。(注意:这里根据字节的域名和headscale的端口填写)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
| map $http_upgrade $connection_upgrade {
default keep-alive;
'websocket' upgrade;
'' close;
}
server {
listen 80;
listen [::]:80;
server_name p2p.mr-h.org;
location / {
proxy_pass http://127.0.0.1:8080;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection $connection_upgrade;
proxy_set_header Host $host;
proxy_buffering off;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /web {
index index.html;
alias /var/www/web;
}
}
|
- 将配置软链接到/etc/nginx/sites-enabled
1
| sudo ln -s /etc/nginx/sites-available/headscale /etc/nginx/sites-enable
|
- 测试,重载,重启nginx
1
2
3
| sudo nginx -t
sudo systemctl reload nginx
sudo systemctl restart nginx
|
certbot申请证书
- 使用certbot申请证书(注意:填写自己的域名)
1
| sudo certobot --nginx -d p2p.mr-h.org
|
执行完申请证书的命令后,可以看到nginx里headscale的配置配置被修改。
使用浏览器访问https://p2p.mr-h.org/web 是否能够正确使用https协议。(注意:1.访问自己的域名。2.已经搭建好了headscale 和 headscale wei ui)
如果上面还是无法使用http协议,可参考我的配置进行修改。(注意:根据自己的域名、域名证书和headsale端口修改))
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
| map $http_upgrade $connection_upgrade {
default keep-alive;
'websocket' upgrade;
'' close;
}
server {
listen 80;
listen [::]:80;
server_name p2p.mr-h.org;
location / {
proxy_pass http://127.0.0.1:8080;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection $connection_upgrade;
proxy_set_header Host $host;
proxy_buffering off;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /web {
index index.html;
alias /var/www/web;
}
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name p2p.mr-h.org;
ssl_certificate /etc/letsencrypt/live/p2p.mr-h.org/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/p2p.mr-h.org/privkey.pem;
location / {
proxy_pass http://127.0.0.1:8080;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection $connection_upgrade;
proxy_set_header Host $host;
proxy_buffering off;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /web {
index index.html;
alias /var/www/web;
}
}
|

